On the Security of the Dandelion Protocol
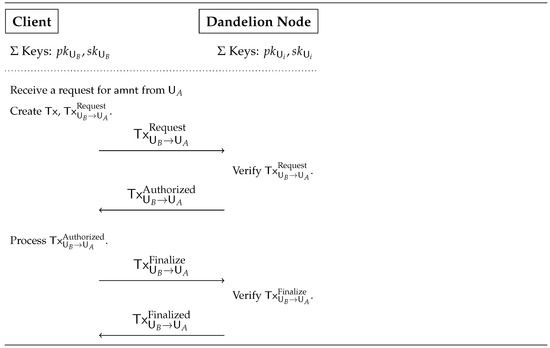
Figure: The Dandelion transaction request message flow
Summary
In this paper, we review the peer-to-peer blockchain transaction protocol, Dandelion, and develop an oracle-based model for its network and security. We formalize a series of security and functional criteria, such as unforgeability, non-repudiation, and immutability, into security experiments. In our model, we consider a quantum-capable adversary who seeks to undermine any of the security criteria while using oracles to simulate and interact with the Dandelion network. We then prove the security of Dandelion in our model with a series of (tight) security reductions as our main result. In addition, we prove that Dandelion is resistant to double-spending attacks.
Keywords
blockchain, post-quantum, network security, security, protocols, privacy, quantum security
2023 Journal Impact Factor: 2.3
Publication date: April 1, 2022
Links
References
| APA | Goncalves, B., & Mashatan, A. (2022). On the Security of the Dandelion Protocol. Mathematics, 10(7), 1054. |
|---|---|
| BibTeX | @Article{math10071054, author= {Goncalves, Brian and Mashatan, Atefeh}, title= {On the Security of the Dandelion Protocol}, journal= {Mathematics}, volume= {10}, year = {2022}, number= {7}, issn= {2227-7390}, doi= {10.3390/math10071054} } |
| DOI | https://doi.org/10.3390/math10071054 |
| IEEE | B. Goncalves and A. Mashatan, “On the Security of the Dandelion Protocol,” Mathematics, vol. 10, no. 7, p. 1054, Apr. 2022. |
| ISSN | 2227-7390 |
Acknowledgement
This research was supported, in part, by the Natural Sciences and Engineering Research Council (NSERC) (external link, opens in new window) and MITACS (external link, opens in new window) .